Instagram is one of the big four social media platforms, and it is growing bigger day after day. This could have been a big security breach with thousands of accounts at stake. However, they haven’t patched all the vulnerability yet. Many are still under the process of being fixed. This security breach was discovered and reported by Indian bug bounty hunter Laxman Muthiyah. He posted on the Internet that a remote hacker can reset your account password. The vulnerability existed in the password recovery method on Instagram. Laxman helped identify the flaw and worked to get the matter known to the right quarters. In the mobile app, the password reset feature allows users to change the password by confirming a 6-digit secret passcode sent to your featured mobile number or email ID. The Passcode expires in 10 mins. During this period, hackers have to try a million-combination using brute force attack. Instagram has rate limiting code to prevent hackers and prevents hacking on many fronts. In other words, hacking can really cause havoc among social media channels. Moreover, there are a lot of hackers who are black-hat and work to make the system bend. Hence better features are needed to make Instagram better.
How did Laxman Bypass this Limit?
Laxman found that this can be bypassed by sending brute force attack from the different IP address. This concurrent attack can easily hack your account without any required interaction from the user. Therefore this is very dangerous.
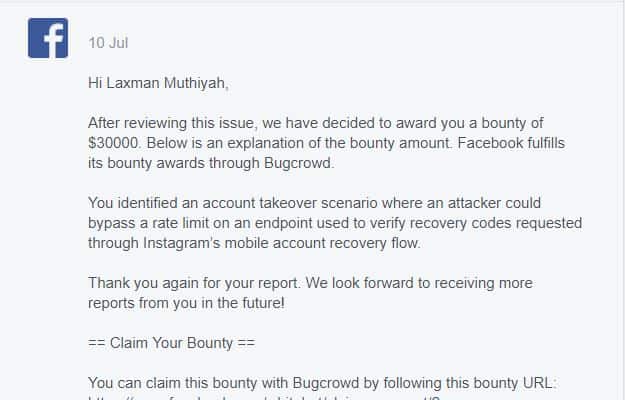
Laxman released a video in which he demonstrated how you could attack an account. He attempted 200,000 different passcode combinations (20%) without getting blocked. He further added that a hacker needs only 5000 IPs to try all combination. Hence this might sound a lot, but it would cost only about 150 dollars to hack an account. This may alarm you a lot but it is the truth. Instagram has patched this security breach and awarded Laxman $30,000 reward as part of its bug bounty program. Hence, we advise all users to enable “two-factor authentication” to drive hackers away. Source – TheZeroHack